Configure an Azure Cloud Account
Configure a Cloud Account
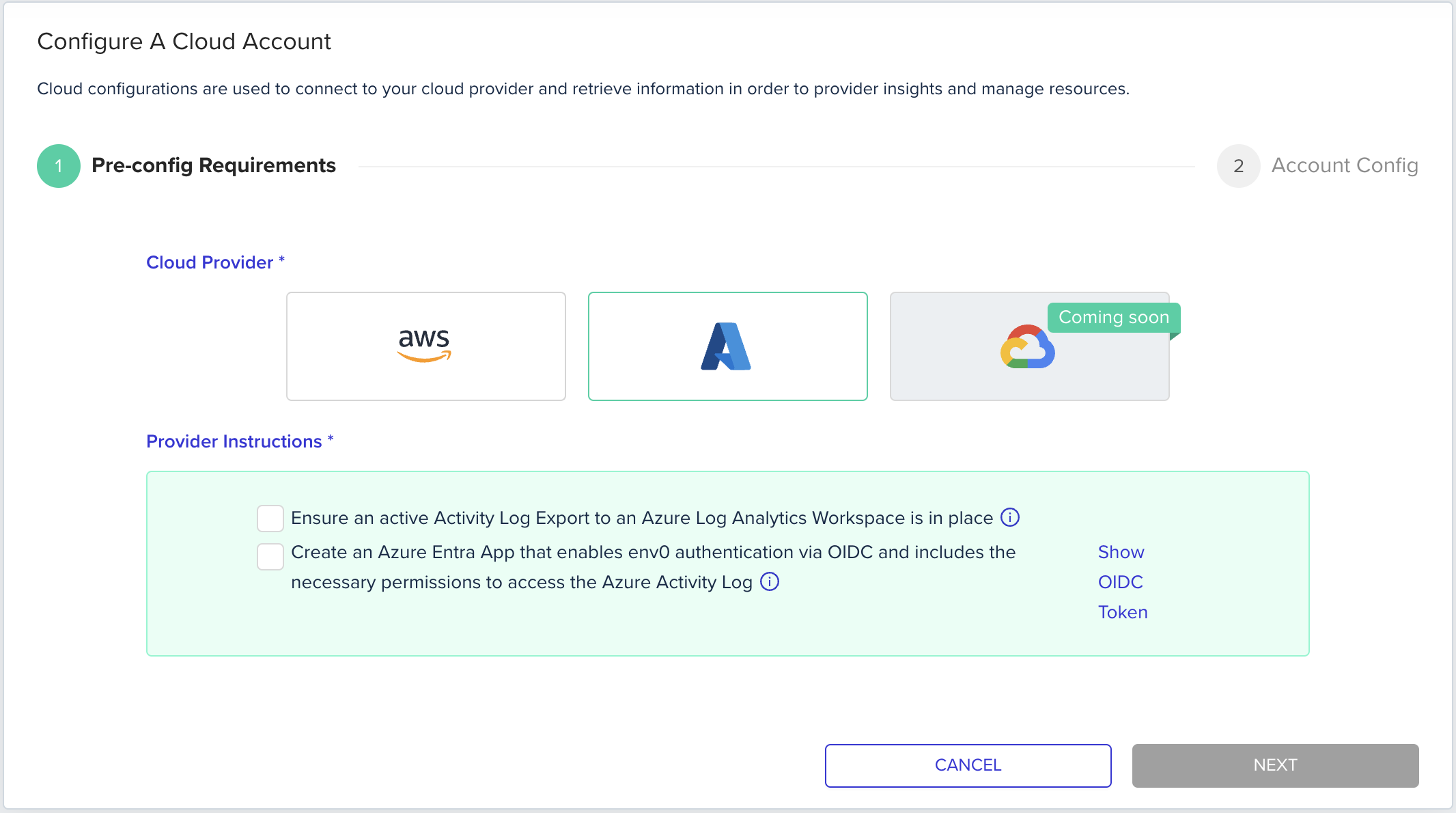
Requirements
Export Activity Logs to an Azure Log Activity Workspace
-
Open the Azure Console and login to the relevant tenant
-
Go to the Activity Log service
-
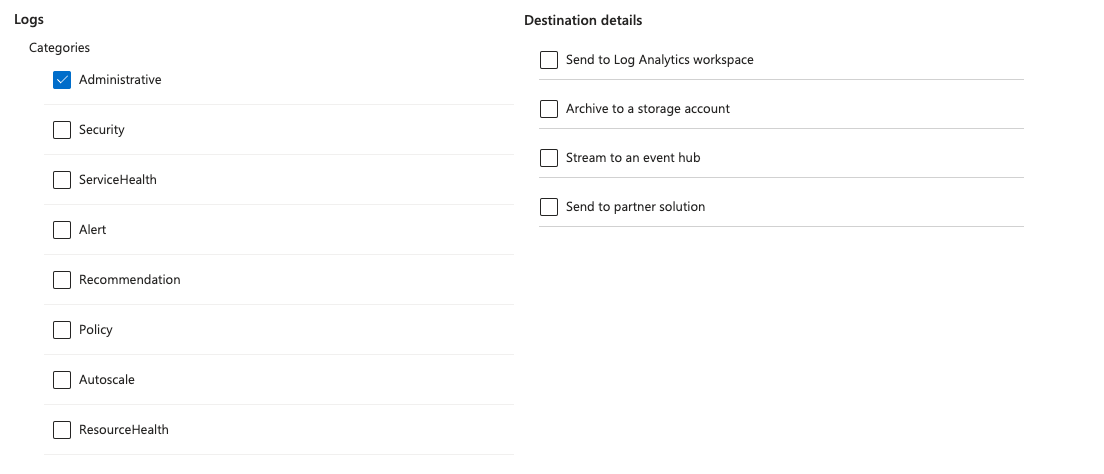
Follow Azure official procedure to send the activity logs to a Log Analytics Workspace
- env0 reads and uses the Administrative logs only:
Grant permissions to env0 via OIDC
- Open the Azure Console and login to the relevant tenant
- Go to the Microsoft Entra ID service
- Follow this procedure to configure a proper App registration
- After the App registration is created, Go to the Log Analytics Workspaces service
- Select the relevant Log Analytics Workspace, and select Access Control (IAM) from the left pane menu
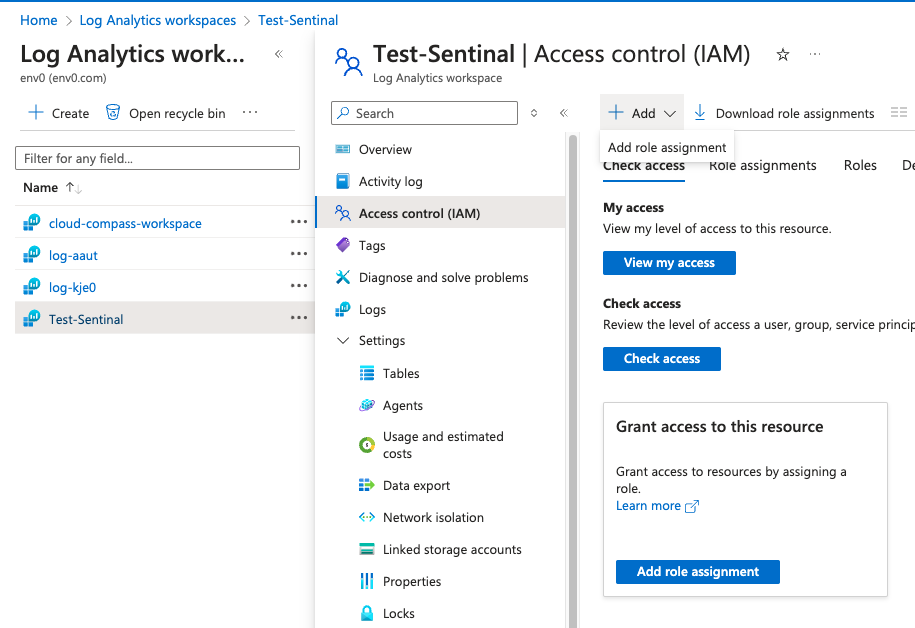
- Click + Add and select Add role assignment
- Add the Log Analytics Reader permission to the relevant App registration
To enrich the data and provide better insights into the account, the Application.Read.All permission is required. This permission enables the app to retrieve Azure AD application details, helping map app IDs to human-readable names for better account understanding.
Adding the Permission in Azure Portal
- Go to Azure Active Directory in the Azure portal.
- Select your app under App registrations.
- Navigate to API permissions, click Add a permission, select Microsoft Graph, choose Application permissions, and add Application.Read.All.
- Click Grant admin consent for
<Tenant Name>under Configured permissions. You must have a role like Global Administrator to perform this action.
Adding the Permission with Azure CLI
You can also use the Azure CLI for this:
- Add the permission:
az ad app permission add --id <APP_ID> --api 00000003-0000-0000-c000-000000000000 --api-permissions 311a71cc-e848-46a1-bdf8-97ff7156d8e6=Role - Grant admin consent:
az ad app permission grant --id <APP_ID> --api 00000003-0000-0000-c000-000000000000
Updated 13 days ago
