OIDC - Retrieving Your Organization Subject Identifier
env0 OIDC token contains a unique Subject Identifier per env0 Organization.
There are three methods for retrieving your subject identifier.
A. From the Credential Form
B. From the App
C. Use Run Task
D. Use env0 OIDC script template
E. Manually from env0 deployment
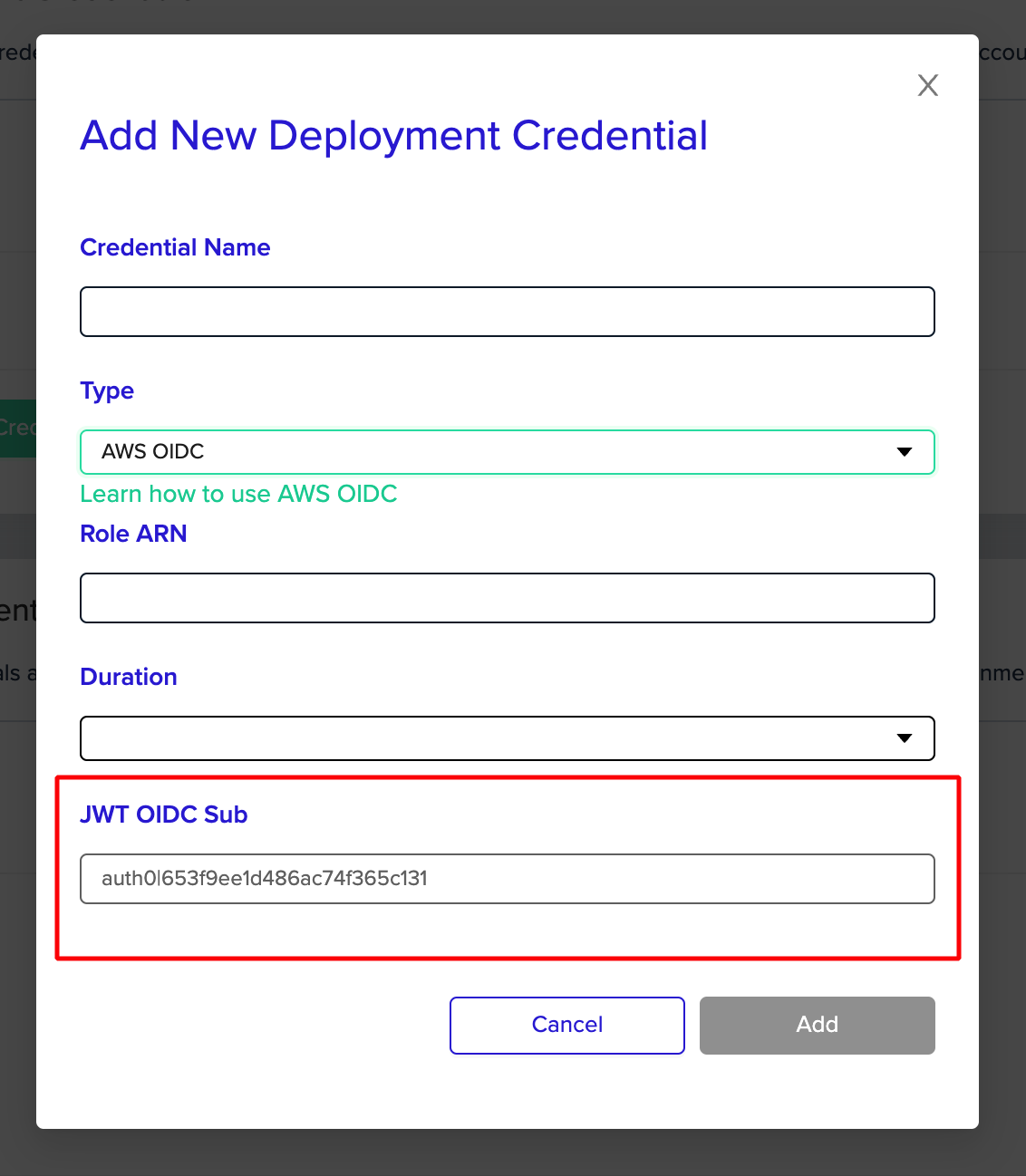
A. From the Credential Form
When creating an OIDC credential in the organization credentials page you can see the sub value in the last disabled form input:
B. From the App
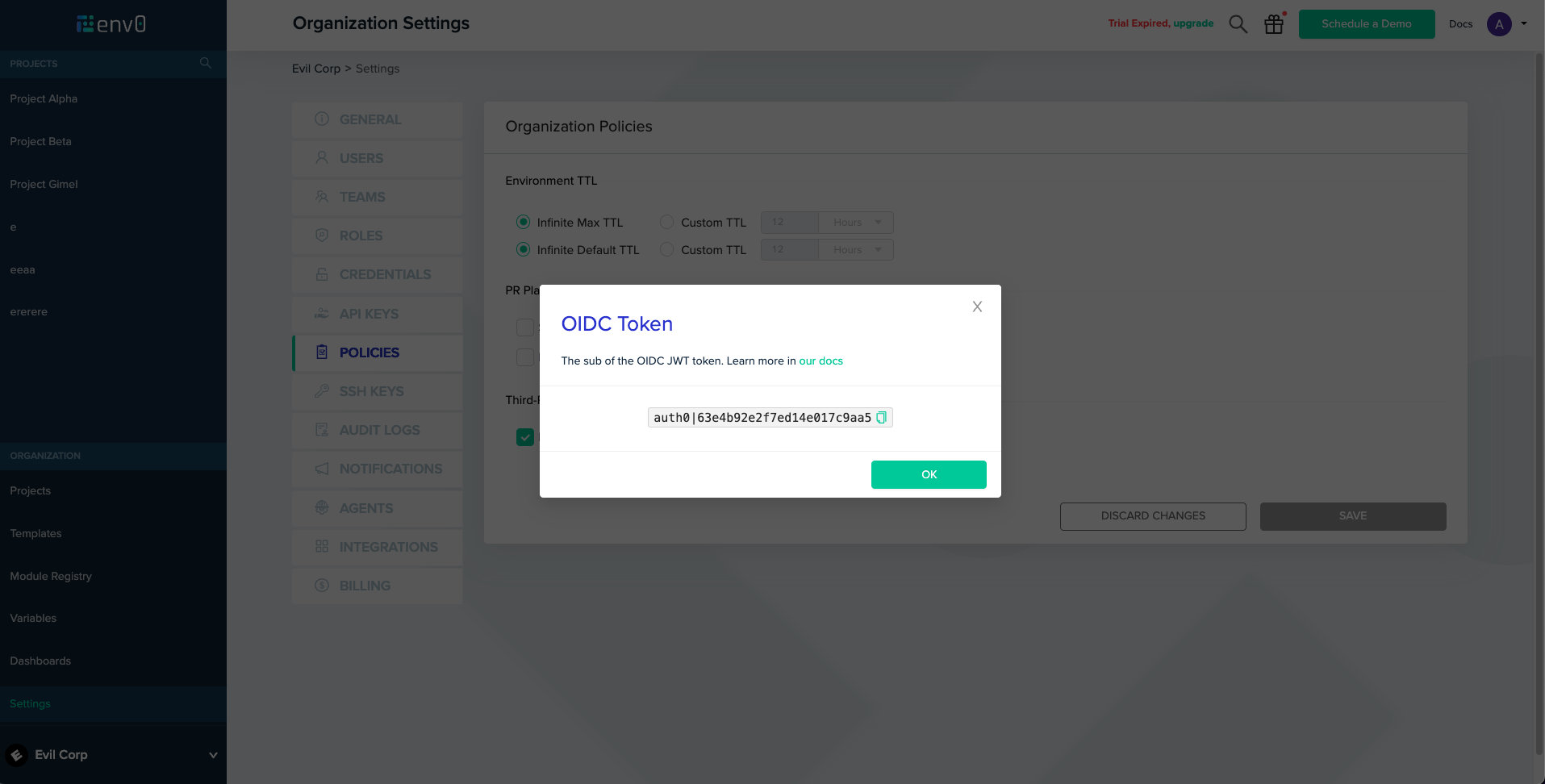
Go to Organization Settings -> Policies
Next to the "Enable OIDC" checkbox, click "show" ( the "show" button will only appear if OIDC is enabled )
C. Use Run Task
This simple node script will help decode the OIDC Token.
- “Enable OIDC”
- Under Organization > Settings > Policy - Check “Enable OIDC during deployments”
- Under Organization > Settings > Policy - Check “Enable OIDC during deployments”
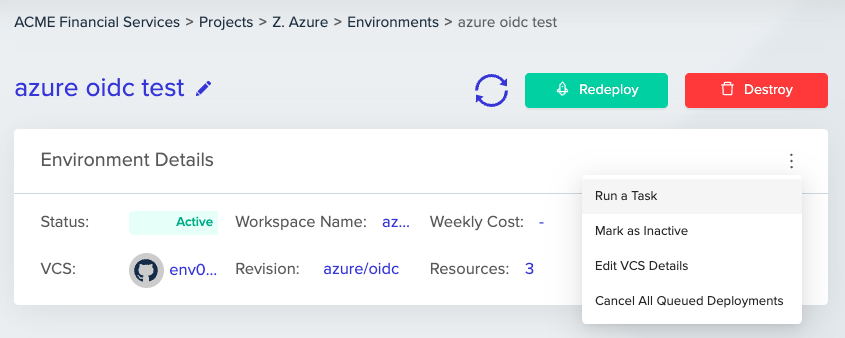
- Run a Task - under any existing env0 environment, select "Run a Task" from the env0 environment menu. Note: You will need administrative access to see this option.
- Copy and Paste this script:
node -e "console.log(JSON.parse(Buffer.from(process.env.ENV0_OIDC_TOKEN.split('.')[1], 'base64')));"- Hit Run a Task and open the console outputs under "Task Commands" step.
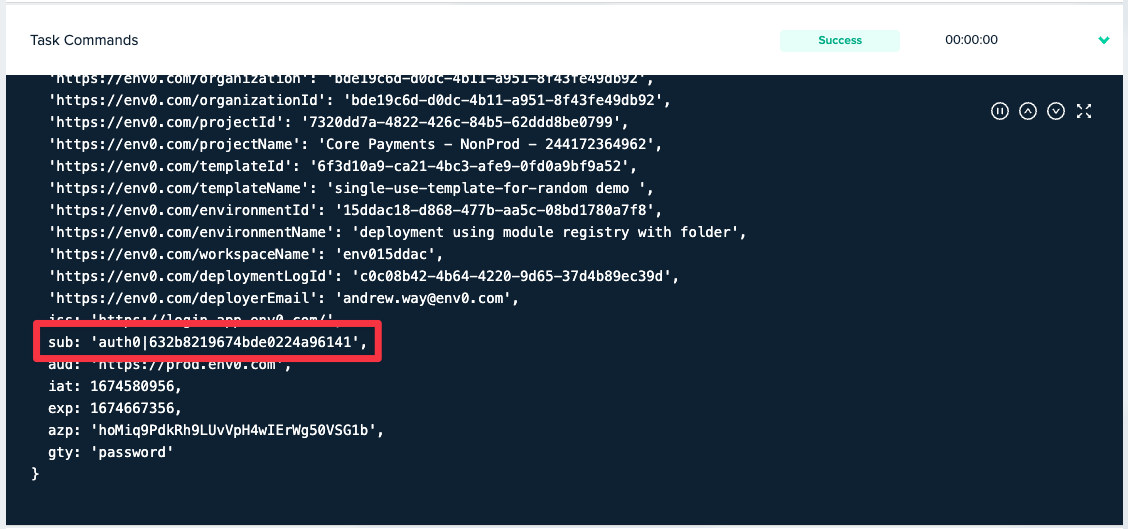
Image of Decoded OIDC Token with "sub" claim highlighted.
D. Using env0 OIDC Script Template
This env0 template, will run a decode script to help you view the contents of the OIDC token.
-
“Enable OIDC”
- Under Organization > Settings > Policy - Check “Enable OIDC during deployments”

- Under Organization > Settings > Policy - Check “Enable OIDC during deployments”
-
Clone or Fork the Repo: https://github.com/env0/customer-tools
-
Run an Environment - from VCS, and configure it with the repo you've cloned/forked to, and the folder path:
iam/oidc/decode-oidc -
This will generate a step in the deployment that outputs the OIDC contents similar to this screenshot:
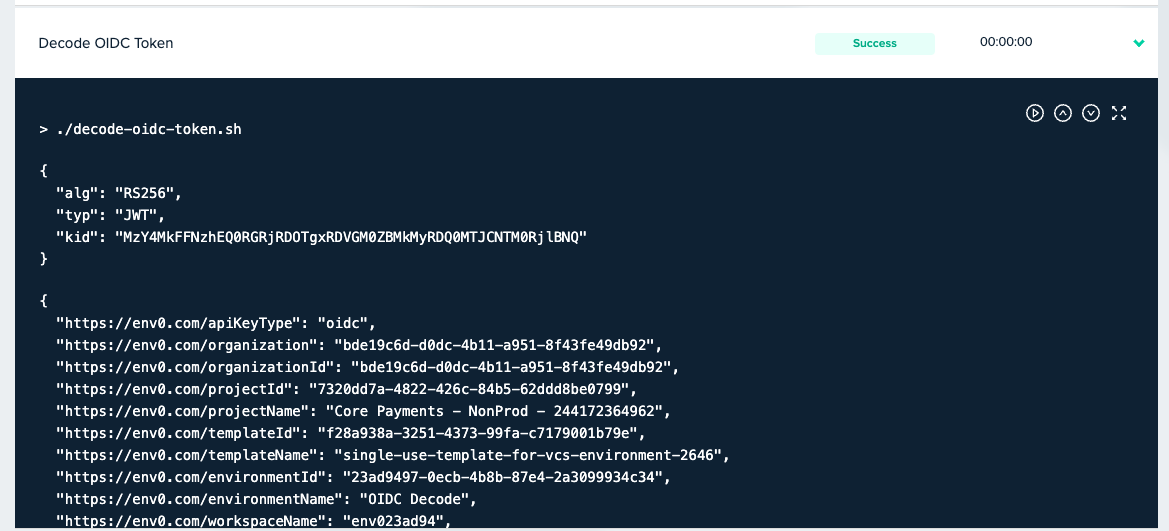
OIDC Token
E. Manually from env0 deployment
To retrieve your organization’s unique Subject Identifier:
-
“Enable OIDC”
- Under Organization > Settings > Policy - Check “Enable OIDC during deployments”

- Under Organization > Settings > Policy - Check “Enable OIDC during deployments”
-
Go to an existing environment and “Run a Task”
-
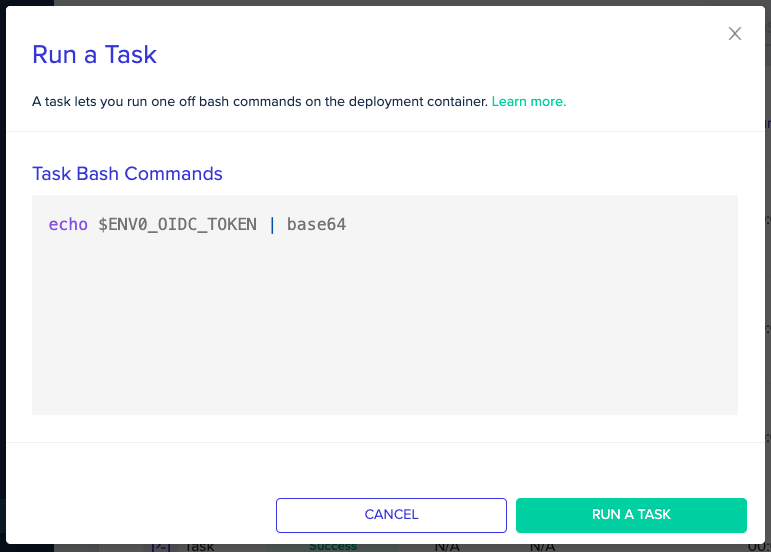
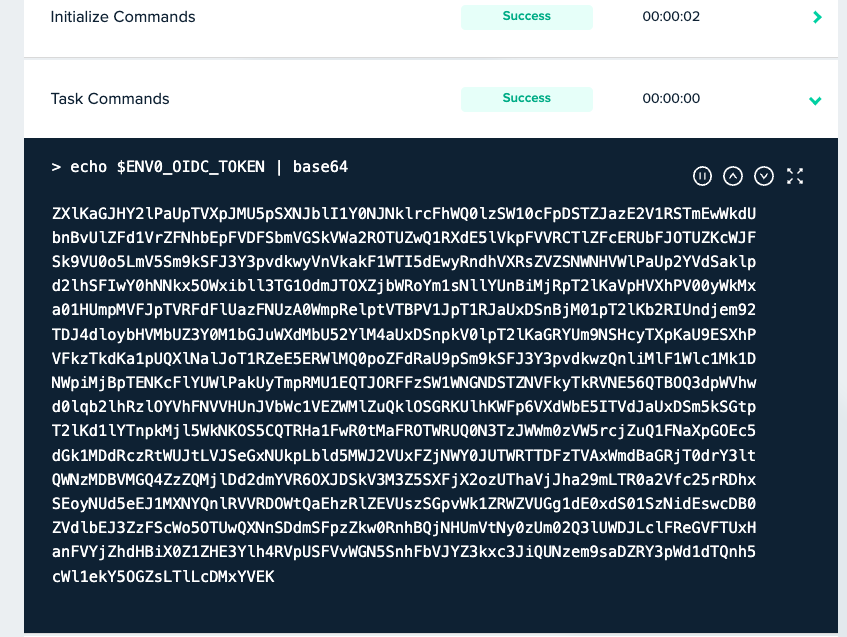
Run the following command:
echo $ENV0_OIDC_TOKEN | base64
-
Copy and Base64 Decode the Token:
echo “ZVXMU5pSXNJblI1Y0NJNklrcFhWQ0lzSW10cFpDSTZJazETmEwWkdU…” | base64 -d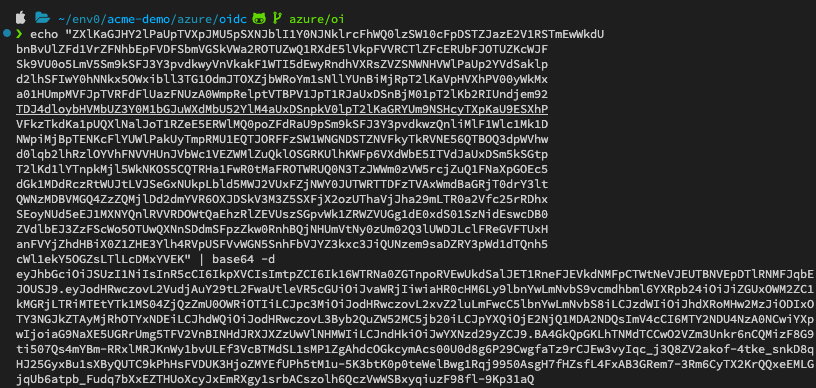
-
Copy the Token and Inspect the decoded token using jwt.io
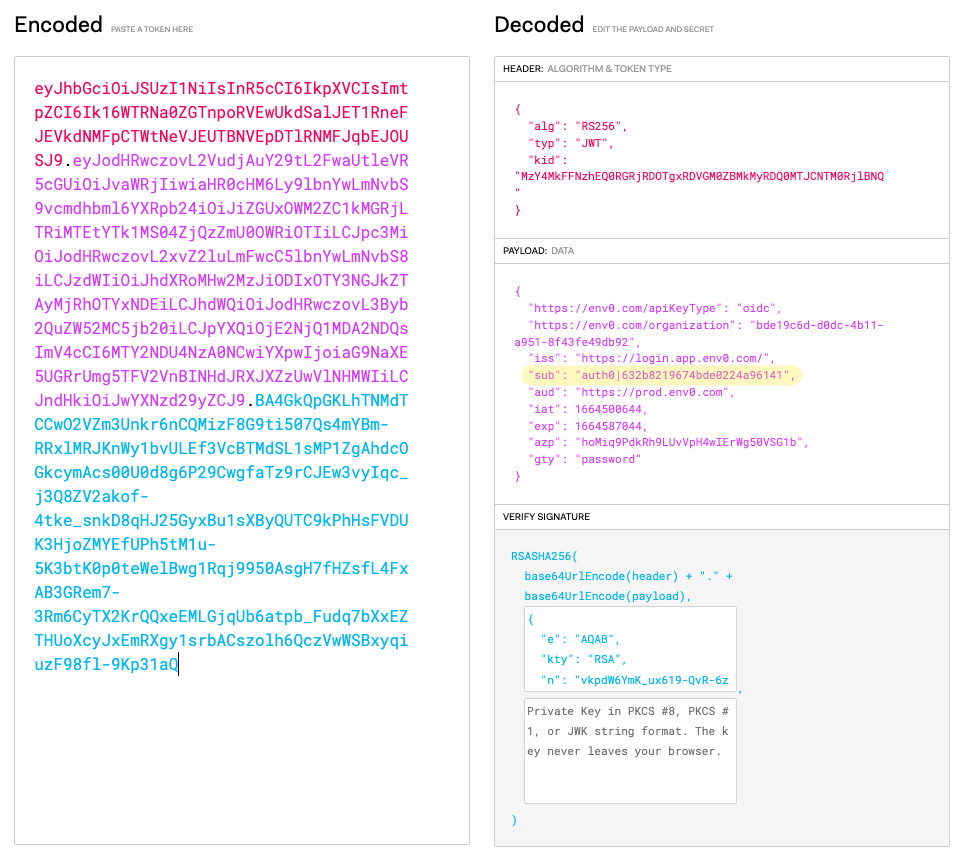
-
Copy the Subject Identifier ”sub” (In this example:
auth0|632b8219674bde0224a96141)
Updated 13 days ago
