OIDC With Azure
How to authenticate the env0 runner using Azure and OIDC
This guide is to help you connect to Azure with OIDC, instead of using a Service Principal.
Overview
This guide will show you how to create an Azure AD App, configure a Federated Credential, and configure env0 to utilize OIDC. The federated credential within the Azure AD app will be configured to accept env0's OIDC token. Refer to OIDC Integrations for more background on env0's OIDC configuration.
Azure AD App + Federated Credential
The Azure AD App will be configured with a Federated Credential in order to accept env0 OIDC token. Using the Azure Portal:
- Microsoft Entra ID > App registrations > "+ New Registration"
- Enter Name: e.g. "env0 OIDC app"
- Select Supported account types if you're unsure, choose “Single tenant”
- Skip Redirect URI
- Register the app.
- Under the “env0 OIDC app” > “Certificates and Secrets” > “Federated credentials”
- “+ Add credential”
- Federated Credential Scenario - Other issuer
- Issuer -
https://login.app.env0.com/ - Subject Identifier -
auth0|xxxxxx(see the section below on “Retrieving your Subject Identifier”) - Name - enter a name (e.g. "env0 OIDC")
- Audience -
https://prod.env0.com
- For using the Azure Provider in Terraform, we need to specify the following variables:
ARM_TENANT_ID- you can find the value in your app registration summary (”env0 OIDC app”) under “Directory (tenant) ID”ARM_CLIENT_ID- you can find the value in your app registration summary (”env0 OIDC app”) under “Application (client) ID”ARM_SUBSCRIPTION_ID- You can retrieve the Subscription ID from the Azure Subscription, or in a Resource Group that you want to use.
Azure App AD App Permissions
In order for Terraform to be able to deploy and manage the resources, we need to associate your Azure AD App with your Subscription or Resource Group
- In this example, I will give the “env0 OIDC app” the “Contributor” role in my “sales-acme-demo” resource group. This means that env0 will only be able to create and manage resources within this resource group.
- Go to the Resource Group (”sales-acme-demo”) > Access Control (IAM)
- Click on “+ Add” > “Add role assignment”
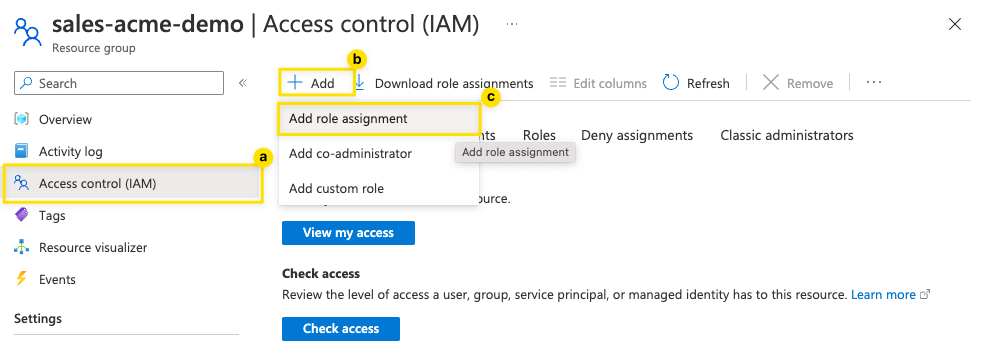
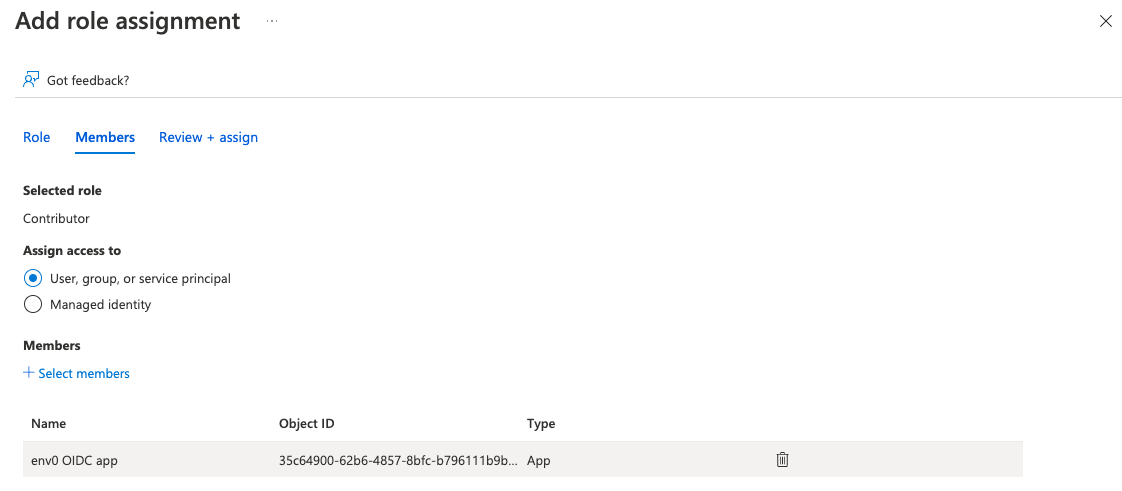
- Select a role (the level of privilege to give to Terraform) - in this case, we choose “Contributor” and hit “Next”
- Assign access to “User, group, or service principal”
- Select a member by “+ Select Members”
- Search for “env0 OIDC app” and hit “Select”
- Hit "Review + assign"
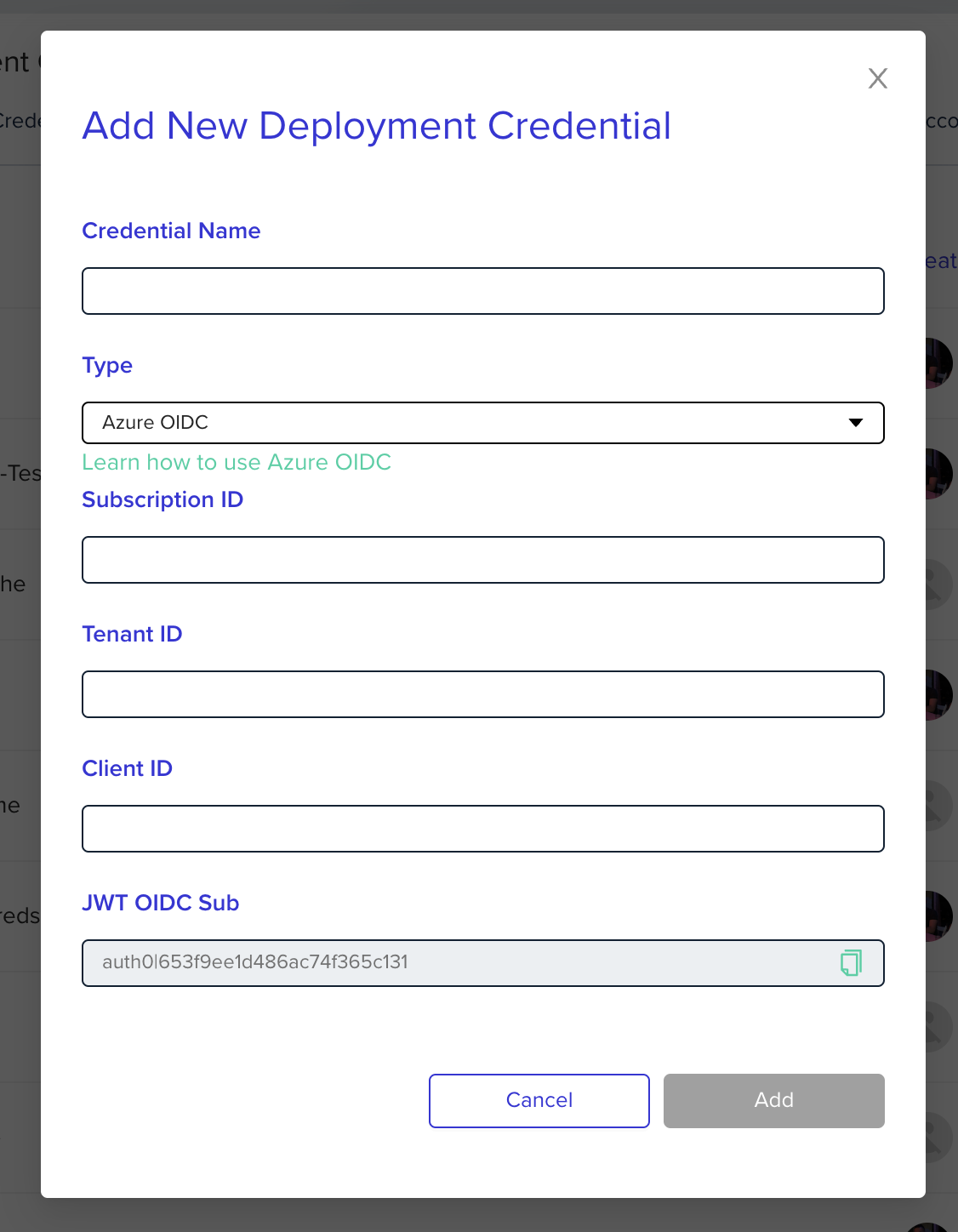
Configure env0 OIDC Credential
Go to the organization's credentials page and create a new deployment credential. Select Azure OIDC type and enter the following fields:
Subscription ID- Azure subscription idTenant ID- Azure tenant idClient ID- Azure client id
Azure Provider VersionMake sure you use a version of the Azure provider greater than 3.7.0.
OIDC did not work for “=3.7.0”
Assign your Credential in your Project
After creating your Organization Credential - don't forget to go into your Project Settings to use the OIDC credential you just created.
Deploying to multiple Azure Subscriptions
Sometimes you want to be able to deploy to multiple Azure Subscriptions in one Terraform workspace. In Terraform / OpenTofu, you can specify multiple azure provider blocks in order to target mutliple subscriptions, see example below:
provider "azurerm" {
features {}
use_oidc = true
//subscription_id = "b48787a1-7145-425f-99af-62cde6c50e31" (optional)
//env0 will use the subscription ID in defined in the Azure OIDC project credential configuration
}
provider "azurerm" {
alias = "test"
features {}
use_oidc = true
subscription_id = var.second_subscription
}
variable "second_subscription" {
type = string
default = "3ef32f99-33d5-4a4f-bf9c-8a3ebb2b0144"
}
resource "azurerm_resource_group" "example" {
name = "env0-example-rg"
location = "eastus2"
}
resource "azurerm_resource_group" "second" {
provider = azurerm.test
name = "env0-example-second-rg"
location = "eastus2"
}By simply, ensuring that the same App Registration created earlier ("env0 OIDC App") has permissions in the both subscriptions; you can utilize one set of credentials to target multiple subscriptions.
Updated 11 days ago
