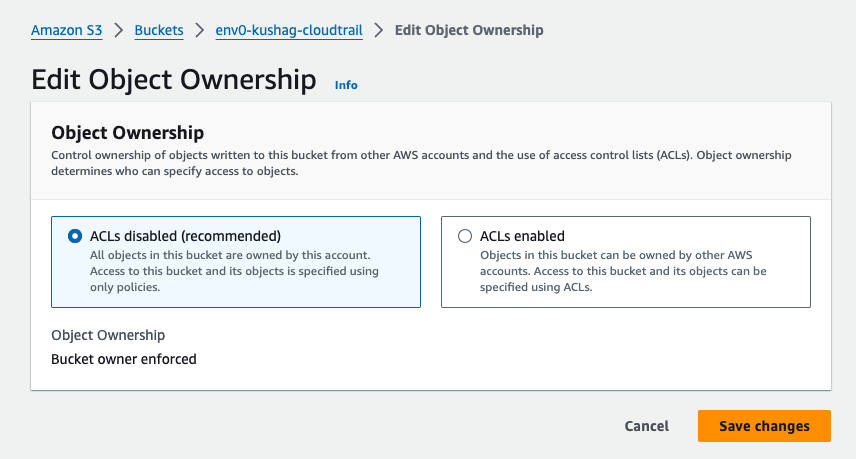
Configure an AWS Cloud Account
Configure a Cloud Account
Additional Costs for Using Cloud Compass with AWSThere could be additional costs for enabling Cloud Compass with AWS that only comes from outbound S3 traffic. This refers to data transferred from S3 buckets to external destinations, which will be charged according to AWS's standard S3 outbound data transfer rates.
Requirements
Ensure Active Cloud Trail
-
Open the AWS Console and login to the relevant account
-
Go to CloudTrail and in the left hand side menu select
Trails -
Make sure the trail is in a Logging status
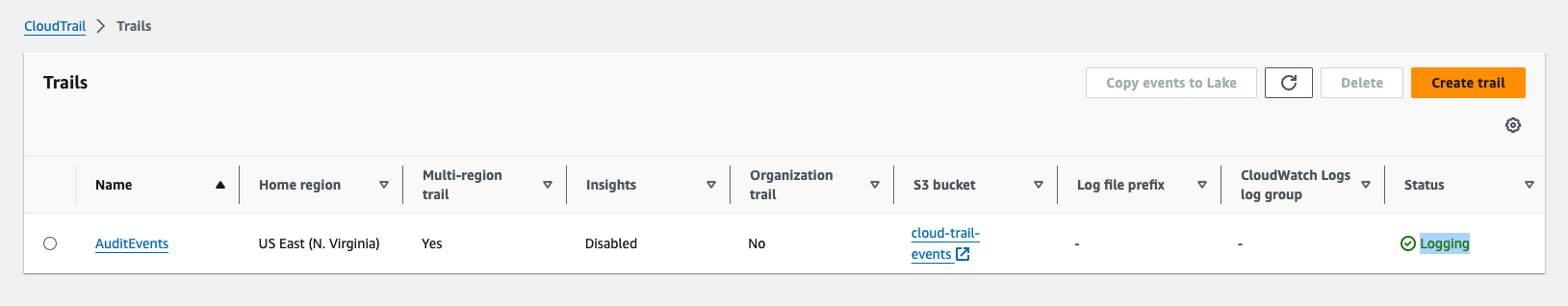
Grant Bucket Permissions
-
Go to S3 Console and choose the relevant bucket based on the name of the S3 bucket in the Trails. You can also click on the bucket name from the previous image.
-
Choose permission tab

-
Go To Bucket Policy and click
Edit -
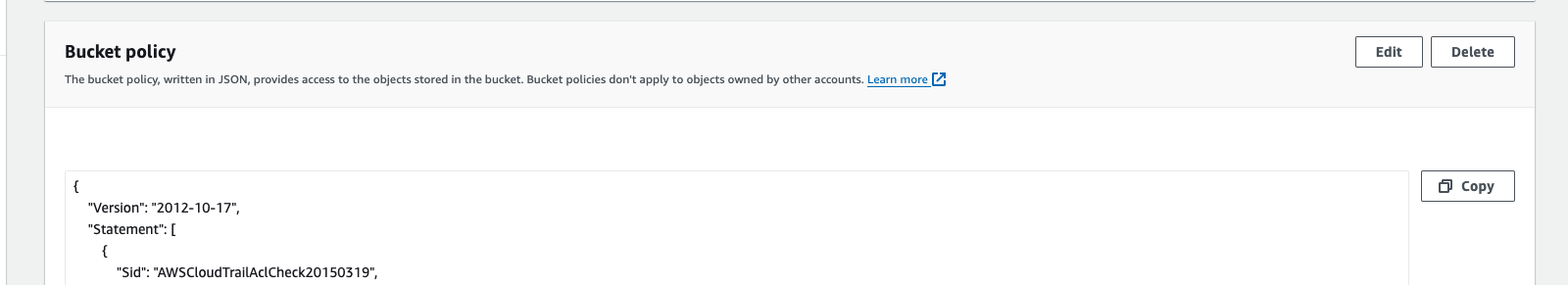
Add the following policy to the list:
{ "Sid": "AllowEnv0ToReadCloudTrailEvents", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::913128560467:role/env0-cloud-scanner" }, "Action": [ "s3:GetBucketLocation", "s3:GetObject", "s3:ListBucket" ], "Resource": [ "arn:aws:s3:::<REPLACE-BY-BUCKET-NAME>", "arn:aws:s3:::<REPLACE-BY-BUCKET-NAME>/*" ] } -
Replace the placeholder
<replace-by-bucket-name>with the bucket name. -
Click on the
Save Changesbutton -
Click on the edit button in the Object Ownership section
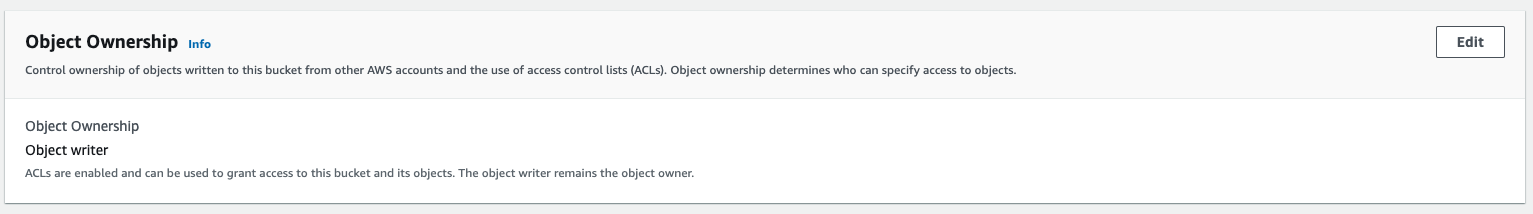
- Select the
ACLs disabled (recommended)option and click on theSave Changesbutton
Object Ownership ModeWe only able to read the cloud trails events when the Object Ownership in mode "ACLs disabled"
Grant Decrypt Permission
-
This requirement is only necessary if encryption is enabled on the trail.
-
You can check if it is enabled by opening the trail and check if
Log file SSE-KMS encryptionis Enabled.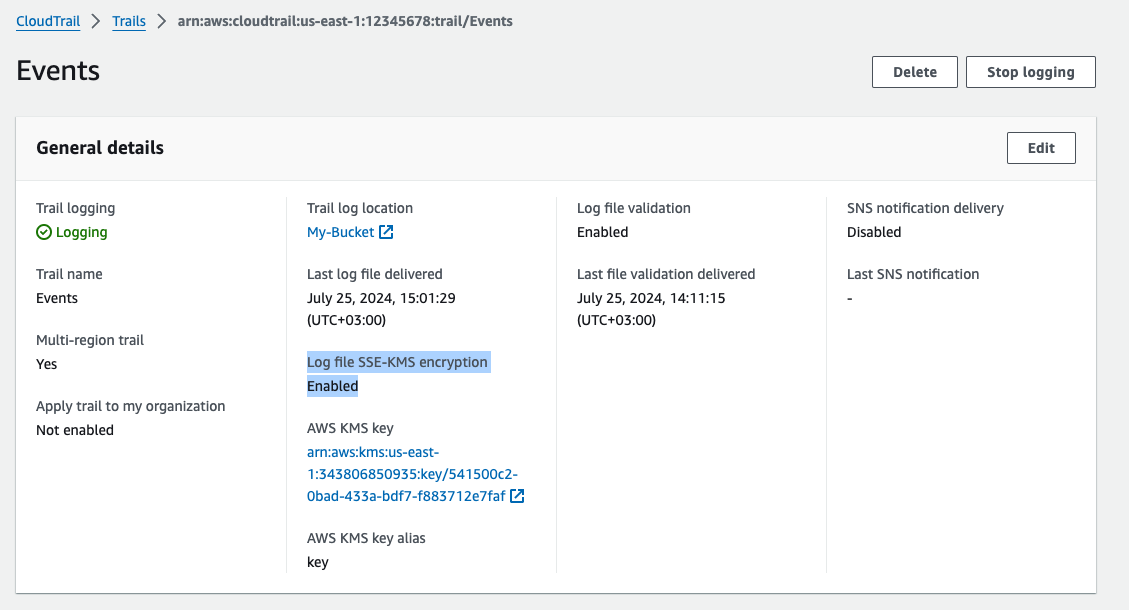
-
If it is enabled, you should grant permission to the env0 role to decrypt the logs.
-
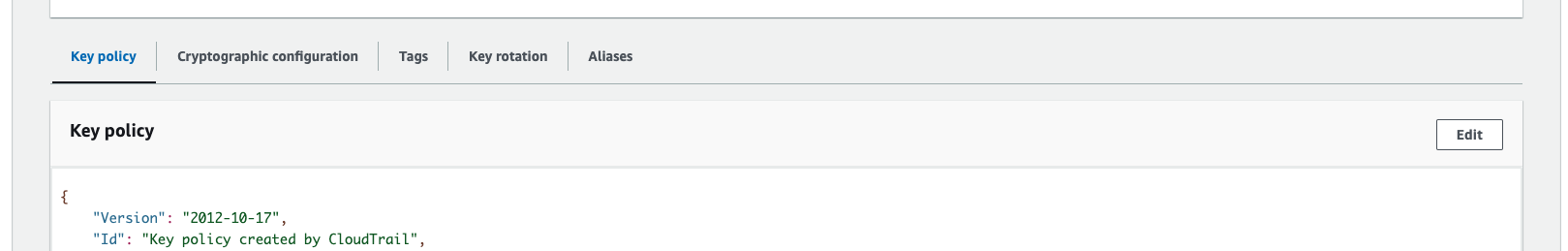
Open the "KMS Key Policy" - by clicking on the key URL from the previous image.
-
Click Edit, and add this policy to the list:
{ "Sid": "AllowEnv0ToDecryptTrailLogs", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::913128560467:role/env0-cloud-scanner" }, "Action": "kms:Decrypt", "Resource": "*" } -
Click
Save Changes
Setting Up Bucket Configuration
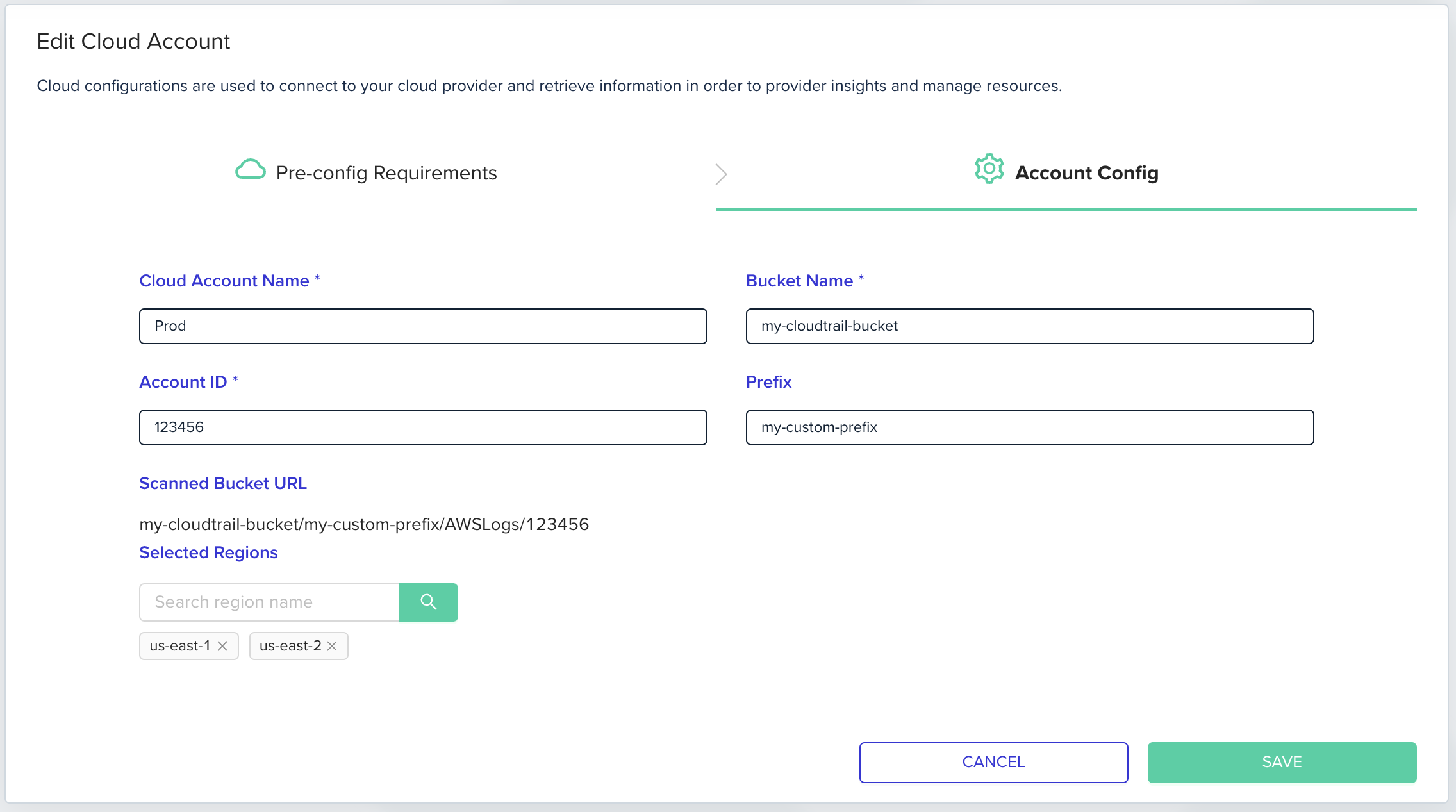
Here you should specify account config including:
- Account name (for identification only)
- Bucket Name [1]
- Account ID [1]
- Prefix [1]
(optional)- this should match the prefix (if specified) when configuring the s3 bucket. See AWS docs. - Regions
[1] These fields are used to build the Scanned Bucket URL which will be used to fetch your cloud events.
Once you have created your account, env0 will start fetching historical data for the past 90 days.
The Insights tab will show that a data fetching run has started. This process might take a few minutes, depending on the amount of events we need to ingest.
Once the data is ready, you will be able to start exploring the dashboard insights. For more information about using the dashboard, click here.
env0 will now run on a daily basis to fetch new cloud activity, ensuring an accurate and up-to-date view of your cloud environment.
Updated 11 days ago