Splunk

Splunk is one of the most popular data platforms for searching, analyzing, visualizing and acting on your data.
env0 has the ability to send all of your deployment logs and audit logs directly to your Splunk account.
Setup
Here are the steps to configure it:
- The integration with Splunk uses the HTTP Event Collector, so you will need to set up it in your Splunk instance:
- For Splunk Enterprise follow this guide
- For Splunk Cloud follow this guide
-
While creating a new HTTP Event Collector you will also create a token. Make sure the token has access to the index you would like to use. You will need this token to configure the integration inside the env0 platform.
-
By default, env0 uses an index called
env0-deployment-logs-indexfor deployment logs and an index calledenv0-audit-logs-indexfor audit logs.
To create an index for audit logs follow this guide. The deployment logs' index name can be it can be overridden. Either create theenv0-deployment-logs-indexindex, or use an existing index. -
By default env0 will use
sourcetype: env0-sourcetype,source: env0-deployment-logs-sourcefor deployment logs andsource: env0-audit-logs-sourcefor audit logs - this can not be overridden. -
There are two ways to configure the integrations:
-
In the env0 app
In the organization's integrations page, click on Splunk and fill the form's fields:
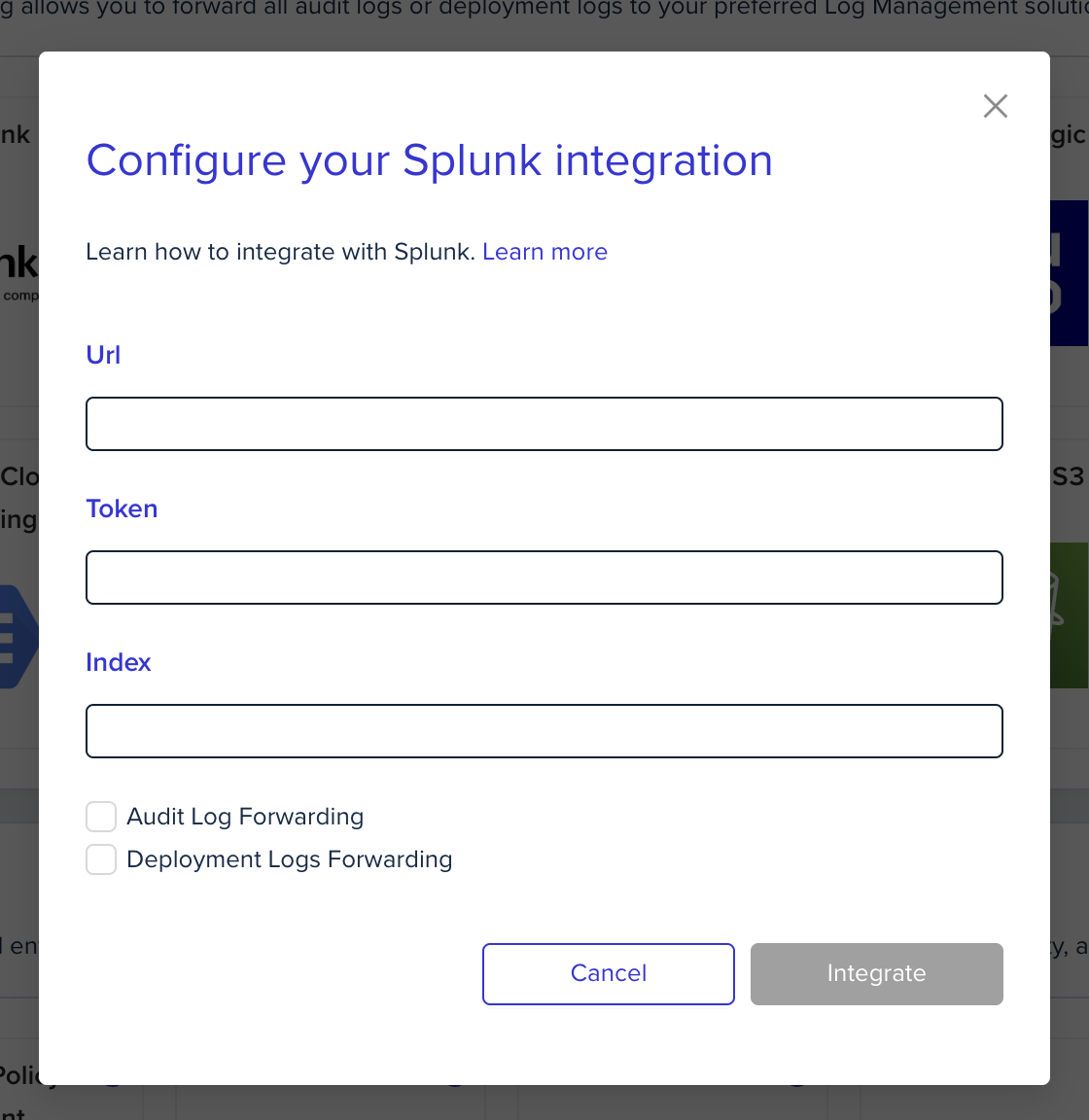
-
Using environment variables
In the env0 platform you will need to configure the following environment variables in any scope you would like to have them:
Environment variable name
Comment
Mandatory
ENV0_SPLUNK_URLThe URL of your splunk instance in the following format: <protocol>://<instance url/ip>:<port> - for example
https://example.splunkcloud.com:8088Yes
ENV0_SPLUNK_TOKENThe HTTP Event Collector token value - this is usually a GUID format token - for example
a90c7a14-8aac-4523-bbbb-dea20352aa4dYes
ENV0_SPLUNK_INDEXThe index you would like env0 to push the data to.
No - Default:
env0-deployment-logs-index
*These environment variables can only override deployment logs forwarding configuration
-
Updated 11 days ago
